Enabling DevSecops for cloud native applications through security automation.
“From the acquisition of Portshift, the Cisco Emerging Technology and Incubation team has been on a mission to enable secure software development for cloud native applications, instilling automation, immediate risk discovery through SBOM vulnerability analysis, and effective security policy management. By empowering application development teams to write application rules via their own tools (Terraform, Helm and others), or security teams to easily provide guard-rails for developers to operate within, application development teams can focus on providing outstanding digital experiences and meeting customer demand in a rapid manner, while enterprises can feel safe to increase their use of containers, serverless functions, APIs, and Kubernetes, knowing they have achieved a strong security posture.”
- Vijoy Pandey, VP ET&I.
Try Panoptica for free today.
Beginning with the launch of Kubernetes in 2015, it has been a rapid growth for the platform and its capabilities. As a testimony to Kubernetes growth, the Cloud Native Computing Foundation, “the open source, vendor-neutral hub of cloud native computing” list countless case studies on their website, discussing tremendous efficiency gains in building cloud native applications and operationalizing them with Kubernetes. In the Cloud Native Computing Foundations annual K8s survey, published late in 2021, according to their respondents, 96% of organizations are now either using or evaluating Kubernetes.
Yet, despite the modernization of the computing environment, and the associated benefits including greater computing scale and faster time to market, one item remains constant, new vulnerabilities are consistently identified, and breaches continue. In March of 2022, a new vulnerability in the popular CRI-O container runtime engine was surfaced. Last December, Log4j impacted over 35,000 packages, “over 8% of the Maven Central repository (the most significant Java package repository),” resulting in “widespread fallout across the software industry,” according to the Google Security Blog.
Separately, RedHat released a report stating that at least 94% of respondents experienced at least one security incident in their Kubernetes environments in the last 12 months. Similarly, a recent report from Veritas found that 89% of organizations view ransomware attacks on their Kubernetes environments as a considerable risk.
At the same time, API breaches are on the rise. This is not surprising as API usage growth has paralleled the rapid increase in Kubernetes usage. Applications running on Kubernetes are primarily microservice built, their many individual components are ideal to interact with other application components, thus driving the growth of APIs.
API-based vulnerability attacks are different in nature from Kubernetes/SBOM or “application infrastructure”-based attacks. While for the latter the hacker goes after vulnerabilities that are introduced when building the Kubernetes application, in the former, the hacker goes after software authentication, authorization and implementation flows resident in the application itself. These types of security flaws are specific to the enterprise’s application, and when such flaws are misused, they can create havoc to the essence of the enterprise. Consider, for example, a banking application with a flawed authorization model where, after authenticating a user, that user can simply swap bank account numbers to access and alter someone else’s “objects” viz-a-viz bank account.
Gartner has predicted that in 2022, application programming interface (API) attacks will become the most-frequent attack vector, causing data breaches for enterprise web applications. In 2021, companies such as LinkedIn, Parler and others experienced API security breaches (5 Real-World API Security Breaches from 2021). Since API services provide access to the data being managed by an enterprise application, API attacks put the data these applications manage at risk. We call these application software issues “application-logic risks”.
To minimize breaches, companies have started to embrace “DevSecOps”, which is defined by IBM (And similarly, by others) as:
“DevSecOps—short for development, security, and operations—automates the integration of security at every phase of the software development lifecycle.”
The positioning of DevSecOps, builds on the concept of "Shifting Left.” As referenced in this April 2022 article by Forbes, entitled “Why Software Shifted Left”,
“The official definition of shifting left, as it relates to security, is the process of implementing or using a tool earlier in the software development lifecycle to enable teams to build more secure applications before deployment.”
At Cisco, we believe an evolution of DevSecOps is that security teams, further partners with application development teams, to ensure that application vulnerabilities, in application infrastructure and their application logic, is viewed in context across the application development lifecycle, which is the essence of our strategic direction with our launch of Panoptica.
Cisco’s Panoptica, The Secure Application Cloud, provides application development and security professionals with a one stop shop to secure modern applications with almost zero friction. The platform consolidates the risks of cloud native applications, whether they are running as containers or serverless Functions, and their APIs, in a single interface. Panoptica provides one seamless prioritized view of workload risks, starting with deep vulnerability analysis, leveraging SBOM and code authentication, extending to the Kubernetes infrastructure and the service mesh, while honing in on specific API security risks.

In the process of building Panoptica, we spoke to dozens of companies from a wide array of verticals across SMB to large enterprise. A constant theme from their security professionals was that application development teams produce APIs too fast and do not always follow best practices. With Panoptica, security teams will have an inventory of all their APIs, and the ability to provide feedback to application development of the risks of their APIs through immediate Fuzz testing, OpenAPI specification analysis and an assessment of OWASP API Top 10 risks.
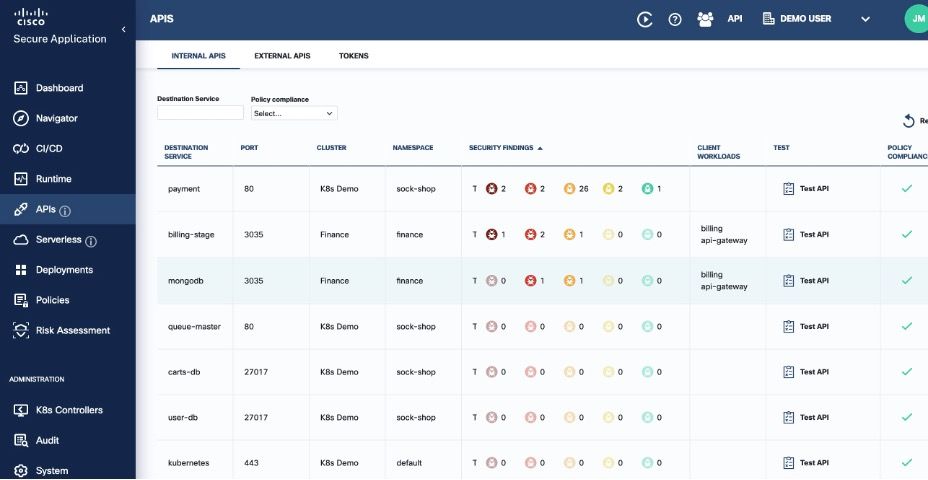
Combine Panoptica’s rich API analysis with the ability to instantly identify vulnerable applications across your environment. The net result is that security teams could have a complete assessment of all their applications immediately. Compare this to the process many security professionals went through last December. As security teams will painfully recall, they lost their Christmas and New Year vacations to Log4J, as they had to dig through every application package in their environment to determine where the vulnerability might exist. Using Panoptica’s SBOM analysis would yield instant inventory of all your applications running Log4J, removing the requirement to comb through every package.

Panoptica completes a 360-degrees view of your environment by evaluating risks of the Kubernetes infrastructure as well as Role Based Access Control (RBAC), while providing a network map of all application connections through Istio service mesh.

Policies can be set across connections (including encryption & application, or layer 7 functionality), deployment rules, cluster events rules, Pod Standards, CI/CD, APIs, and more. Policies are declarative and can be introduced directly from development teams using Terraform or Helm, generated by security teams, or implemented through Panoptica’s Policy Advisor, based on its evaluation of the application traffic.

From acquisition to the launch of Panoptica today, it’s been a whirlwind 18 months for the Portshift, now Cisco ET&I team. We are excited to see Panoptica in action at your company.
Get started with Panoptica for free today in your own environment.





